Fundamental Mechanisms of Regulated Cell Death and Implications for Heart Disease | Physiological Reviews
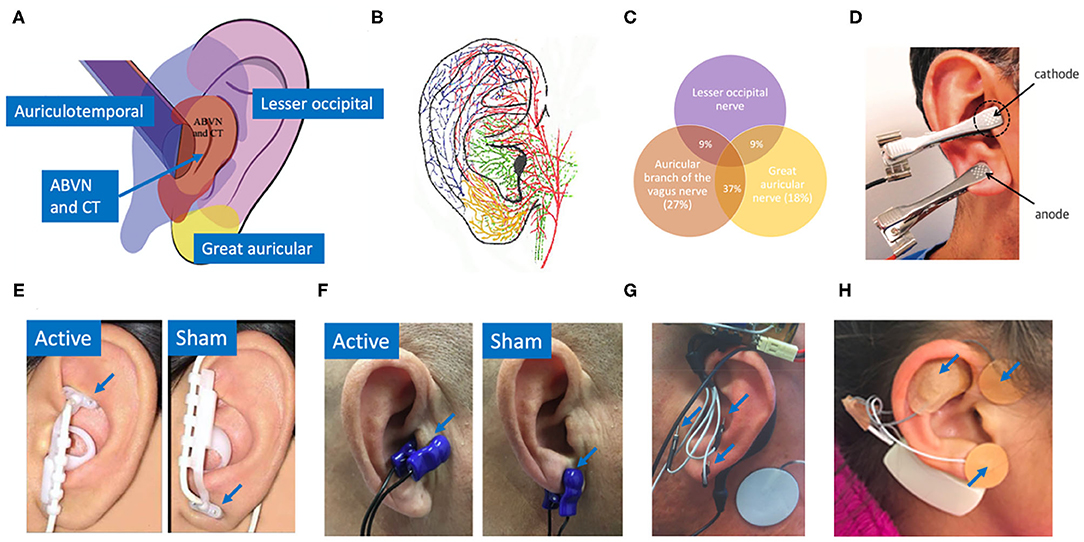
Frontiers | Auricular Vagus Neuromodulation—A Systematic Review on Quality of Evidence and Clinical Effects
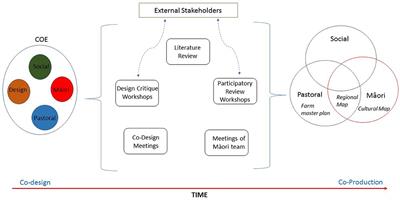
Frontiers | Pursuing Plurality: Exploring the Synergies and Challenges of Knowledge Co-production in Multifunctional Landscape Design
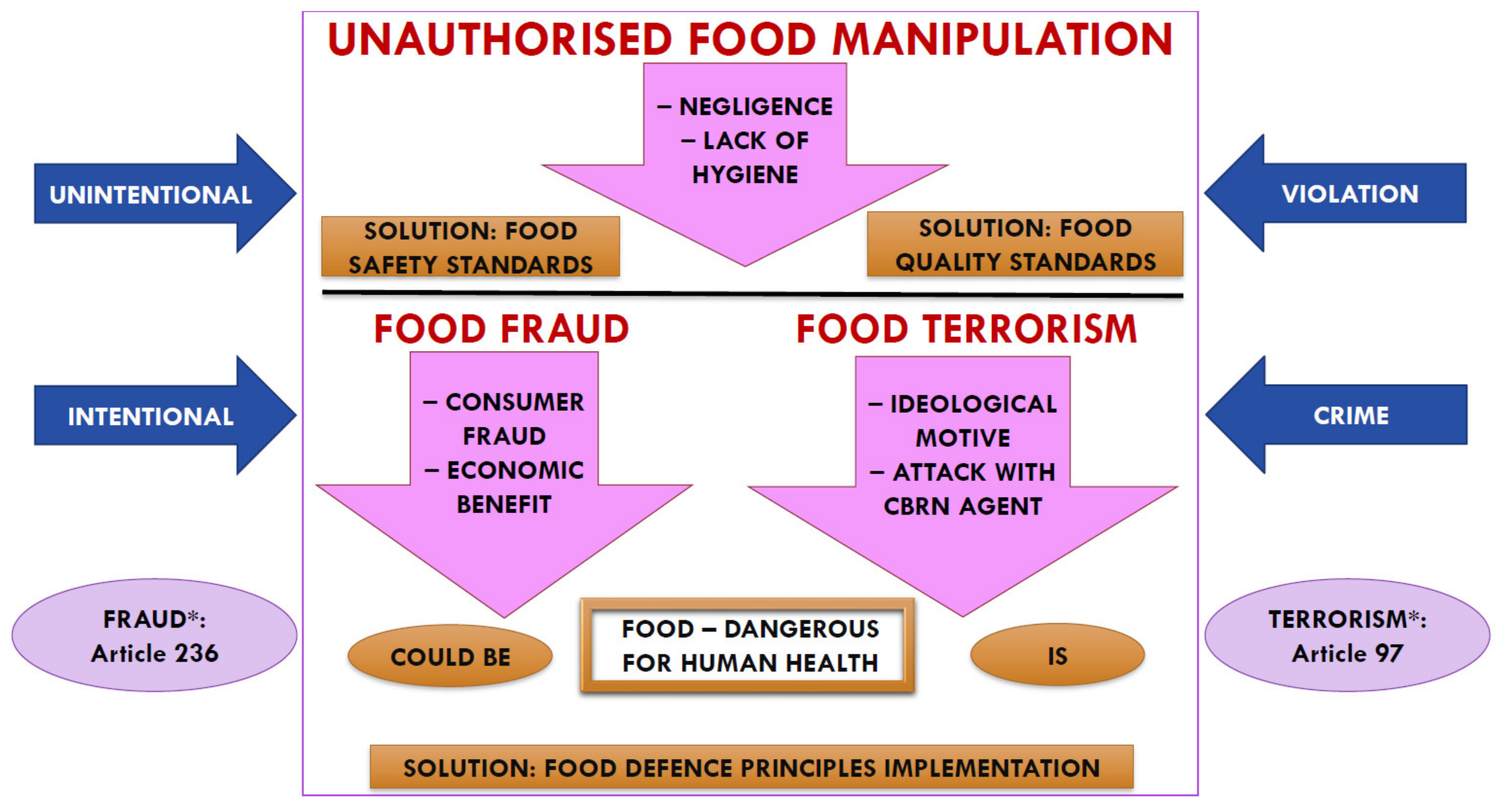
Foods | Free Full-Text | Unauthorized Food Manipulation as a Criminal Offense: Food Authenticity, Legal Frameworks, Analytical Tools and Cases